Facilities Management is one of the most integral roles in the operation, development and maintenance of real estate facilities and communities.
More important than ever is the need for facilities managers to understand and use technology. For commercial real estate, the ability for workplace and office management systems to aggregate data, which drives crucial decisions about how to run the facilities and people flow, will be critical in shaping user experience and operations of buildings. Identifying and implementing the right technology is a chief responsibility of facility managers.
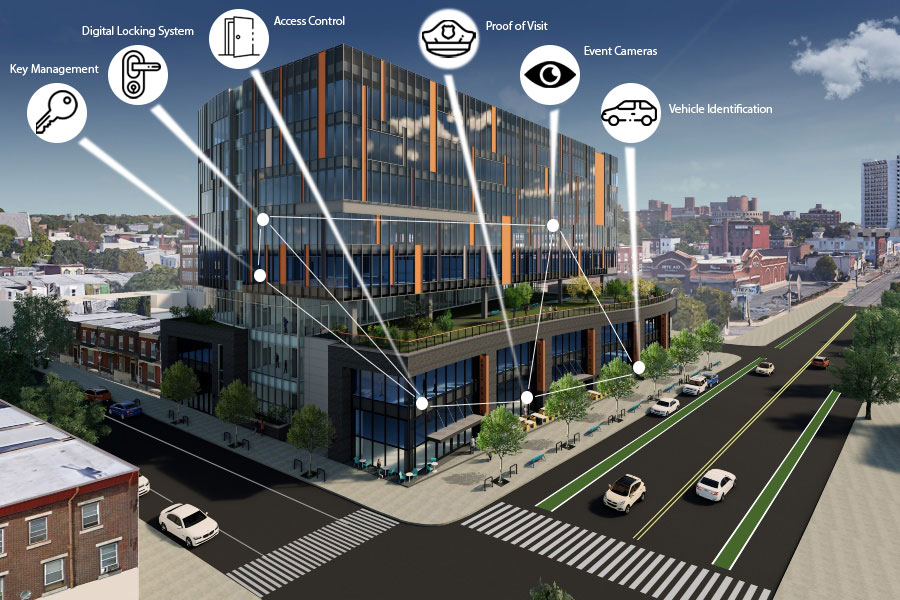
People:
Mobile Credentialing
The foremost objective of a facility manager is creating an accommodating work environment for employees and tenants. This serves many broader goals, including attracting and retaining top talent and tenants, improving efficiency and productivity, and creating a positive building culture.
One of our major roles as a security integrator is to constantly stay on top of technology and improve our services to make sure we help our clients stay one step ahead.
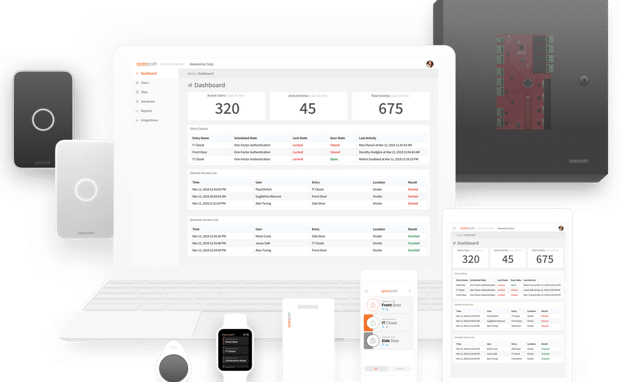
One growing trend we’re seeing is smartphones being used to create mobile credentials for access control systems. It’s made possible by the use of the cloud-based access control servers and delivers a higher level of security, convenience, and savings.
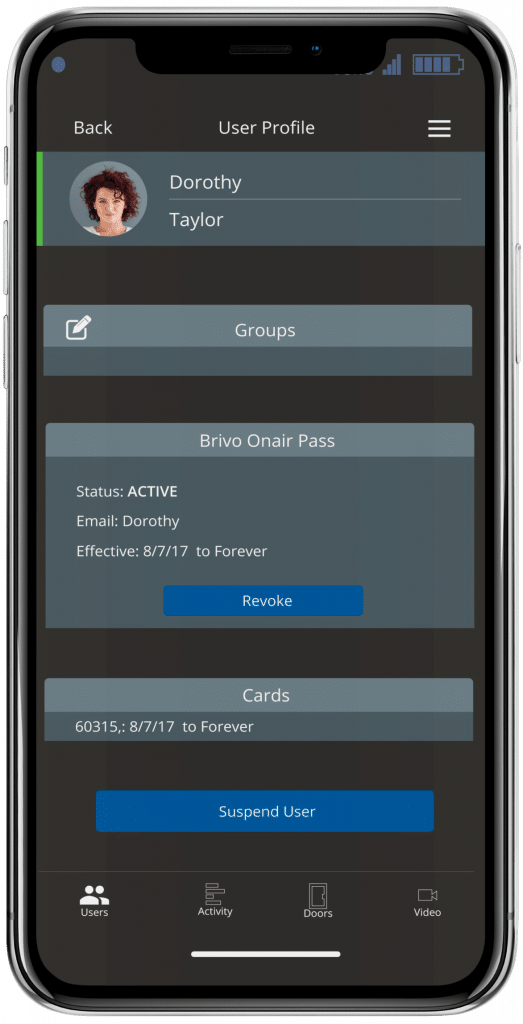

Benefits of Mobile Credentialing Technology
Smartphones require possession of the device, a personal identification number or biometric verification to unlock it, the app and downloaded credential. Facility managers may add a second authentication factor such as a PIN entered into the phone’s keypad.
The cost of the phones and the personal data they store make it unlikely they will be loaned to another employee, lost or stolen – all potential problems with plastic access cards. A smartphone’s built-in GPS enables managers to precisely locate each device (and owner).
There’s no need to carry an access card in a wallet or wear it hanging from a lanyard. Most employees routinely keep their smartphones with them throughout the day. Visitors to the facility can receive an invitation to download a credential and app before arriving, eliminating the need to check-in at the front desk and register for a temporary badge.
With a mobile credentialing system in place, there is no need to procure, store, handle or print physical badges. Imagine the investment of time and money a large university makes issuing thousands of new credentials to incoming students each fall.
Facilities Upkeep + Improvement
Capacity and Occupancy Management – People Flow
From retail shops, to break rooms and conference spaces, to visitor lounges, every organization is challenged with reducing liability and enforcing new occupancy thresholds. While putting up signage is an inexpensive way to notify people of a new capacity threshold, it’s often ignored and therefore ineffective. Stationing additional staff outside doors to count entries and control crowds one way to track capacity, but it is inefficient and often expensive, especially if you have multiple entries into a space. Not to mention, adding staff can put more people at risk.
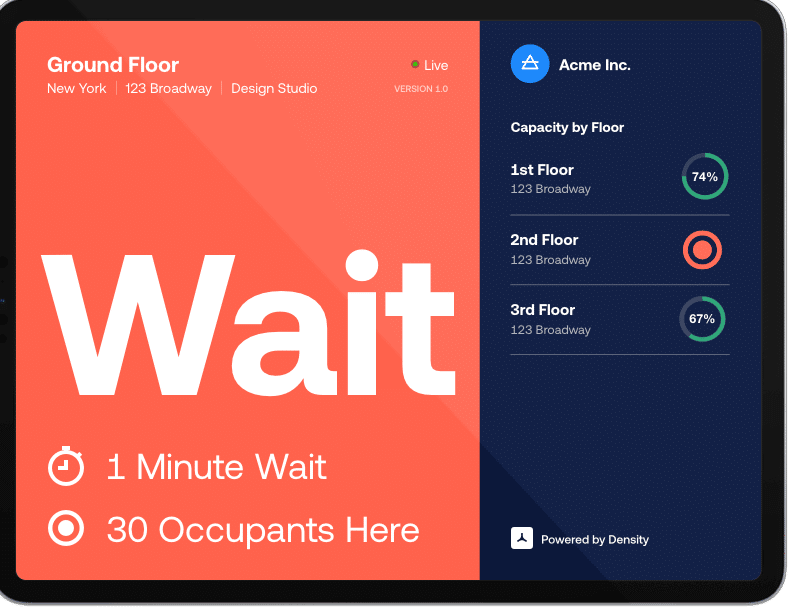

Implementing technology that combines access control with occupancy management is a smart, cost-effective way to enforce capacity thresholds, while still keeping your organization safe and secure. When choosing an occupancy tracker system, you’ll want the ability to change or adjust the threshold of your occupancy counter as needed, easily add or remove credentials at any given time, and systems that mitigate tailgating.
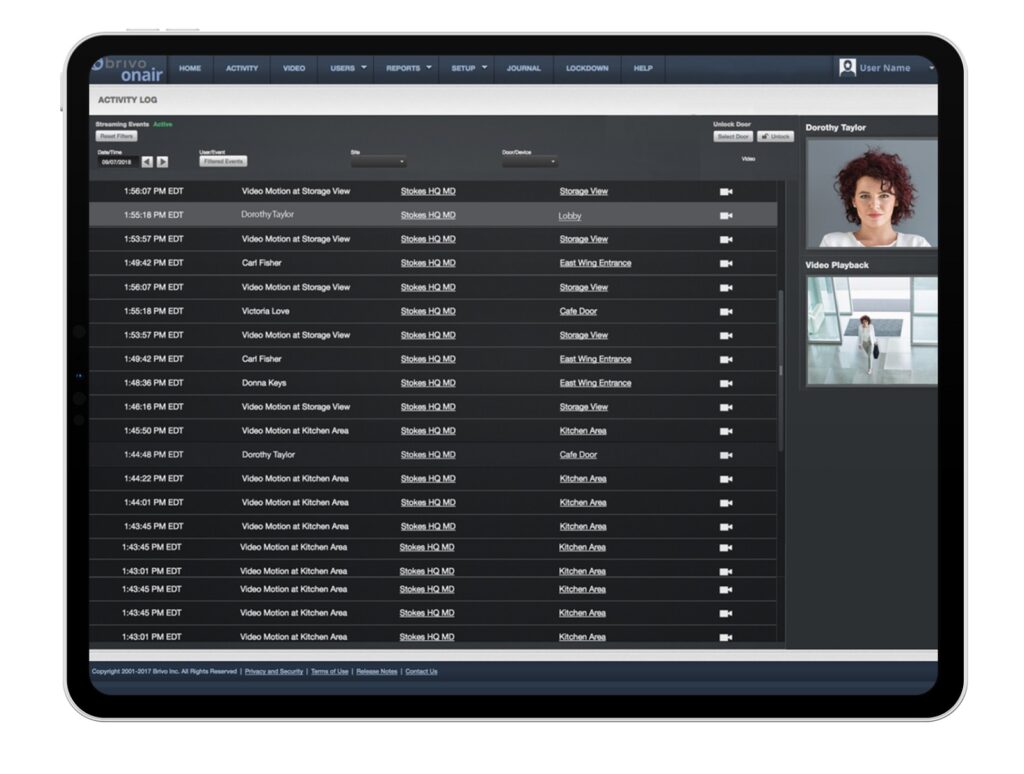
With real-time access tracking and audit trails, Wilco’s cloud-based architecture allows organizations to easily manage their space remotely, as well as the option to integrate with occupancy sensors, capacity counters, and more software for a more robust occupancy tracking solution.

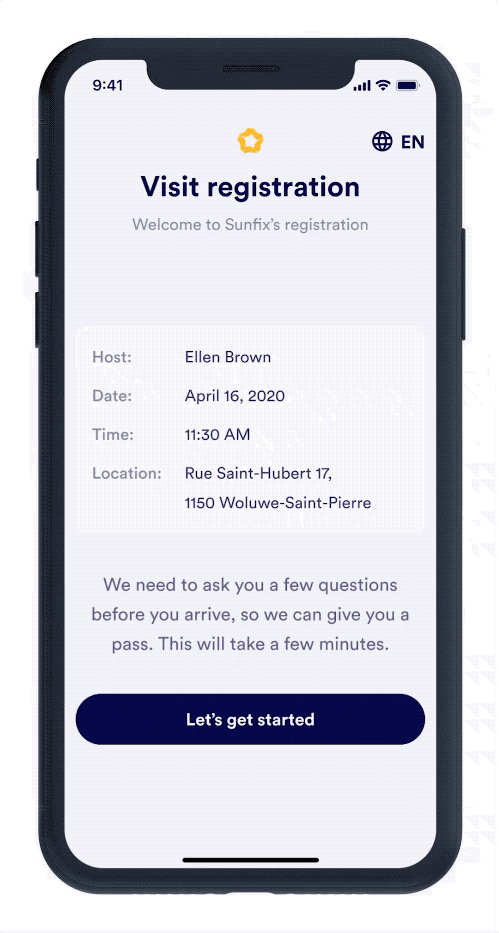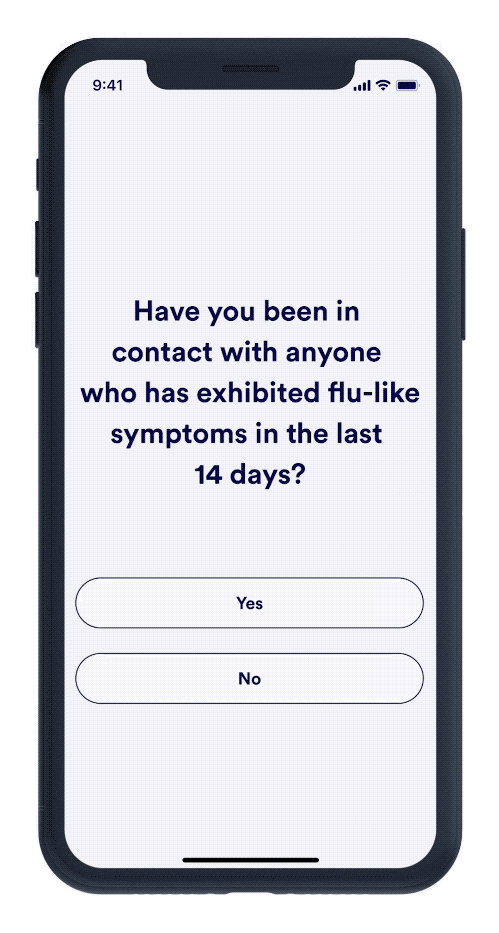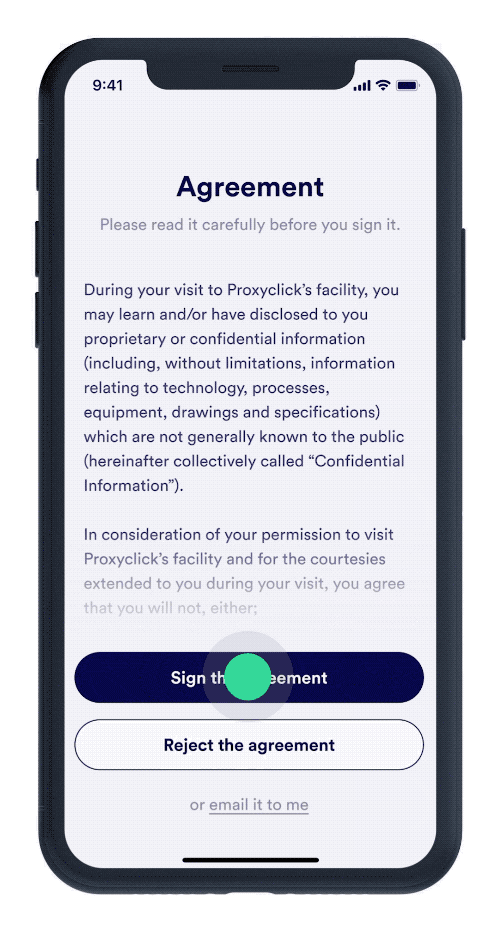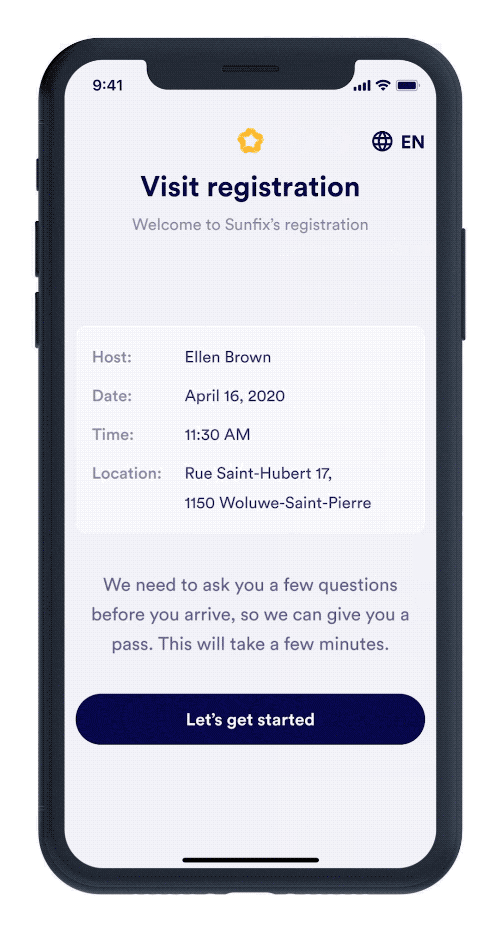
Visitor Management
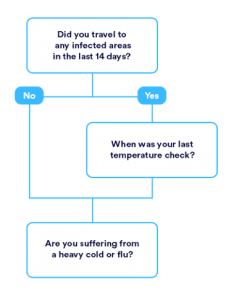
New World of Work
An interview with Proxyclic and Brigitte Daniel, Executive Vice President of Wilco.
Occupancy Management
Measuring Social Distance
Monitor Capacity
Clean with Purpose
Communicate Air Quality
TECHNOLOGY INTEGRATION
Smart Integration
At Wilco, we pride ourselves on being a premier system integrator, and our foundation is built on our 40 years of low volage wiring services. We evaluate each of the current client subsystems and then use our role as trusted technical advisor to lay out a plan for integrating new technology and systems into the existing infrastructure.
As technology and access control solutions have matured and evolved, we work to help define the process and roles related to the systems, such as Access Control, Video, and Intercom/Paging. We coordinate all of our work with the IT organization that controls the technology architecture for the organization, then assist in planning the framework that defines the standards by which ‘systems’ (software and hardware) are evaluated and implemented.
While integration is an asset for virtually any security installation, it becomes vital when discussing critical infrastructure. That might include a water district with many remote sites or a financial data center. These challenging locations go beyond the basics and may require blending wireless technology, intrusion, fire and voice and data systems.
Today, many enterprise organizations require the integration of a dozen or more disparate systems. Converging complex system functionality is a major challenge for most security integrators. Only a small handful have the staff and proven expertise to handle this level of multifaceted integration.
